Binary Used: Infected by accessing the web site www.magnetikum.cz
Details about the files used in this scenario.
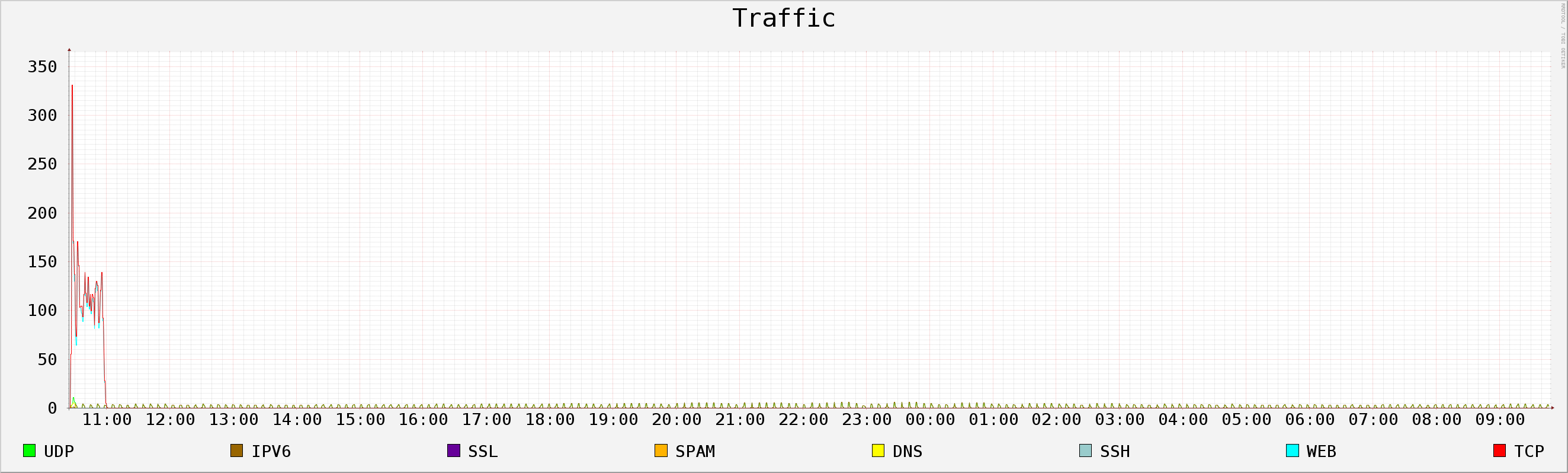
This file is a plot of the mayor features of this traffic during his whole life time.
This file is an RRD file containing all the mayor features of the traffic so you can plot it or analyze it.
This file contains the web logs of the capture extracted by the command:
These are the web logs, but each field is separated by a —.
Description of the weblogs

Thu May 15 10:24:02 CEST 2014 win15 started
Thu May 15 10:27:50 CEST 2014 infected with www.magnetikum.cz
It did not rebooted! and it access completely diferent websites!
Fri May 16 09:48:48 CEST 2014 poweroff because it was doing nothing!
File 2014-05-16_capture-win15.pcap
These files were generated as part of the Malware Capture Facility Project in the CTU University, Prague, Czech Republic. The goal of the project is to store long-lived real botnet traffic and to generate labeled netflows files. Any question feel free to contact us to sebastian.garcia@agents.fel.cvut.cz.
You are free to use these files as long as you reference this project and the authors. See http://mcfp.felk.cvut.cz